2024 N1CTF Reverse 方向 Writes UP
ReFantazio 三血,嘻嘻
ezapk

enc 注册在 libnative1 里面,加密逻辑在 libnative2 里面,在三处 call 寄存器的地方下断点



得到加密逻辑
1 | # iusp9aVAyoMI 异或 rand() |
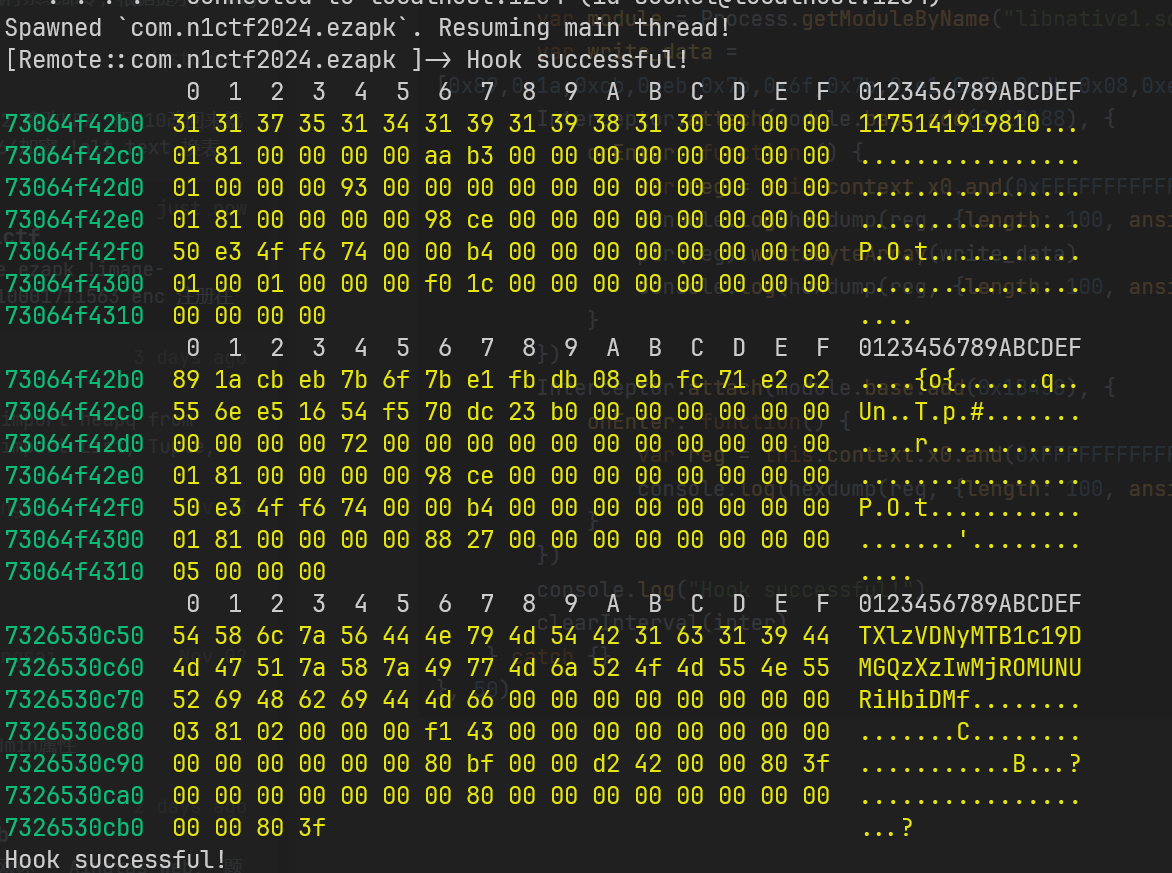
由 RC4 的对称性可以想到一个简便解法,用 frida 下断在 JNI 函数处,覆写 GetStringUTFChars 得到的内存地址

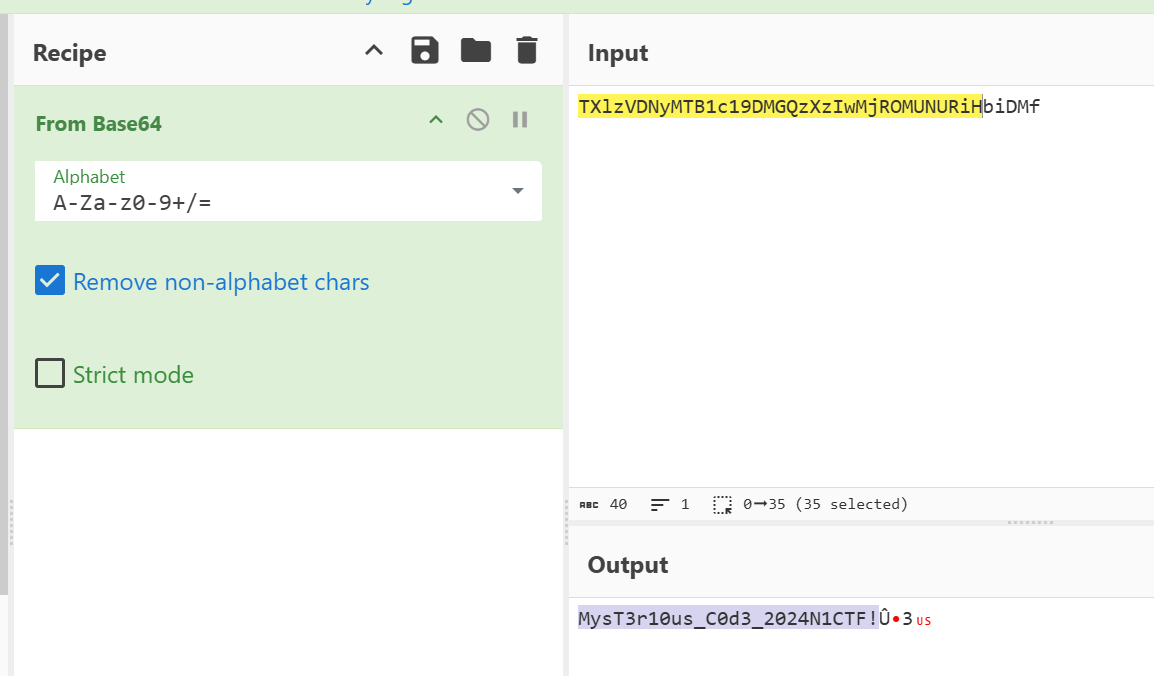
然后再在 ret 的位置 hook 拿到解密后的内容就可得到 flag
1 | var inter = setInterval(function() { |
ReFantazio
三血嘻嘻
到手发现一个很大的 so,ida 查看字符串发现 frida 字样,那么大概是个内置 frida-gum 的程序
第一步,先还原符号
去拉一份最新的 frida 源码,先编译一遍,生成 frida-android-arm64 后修改内容
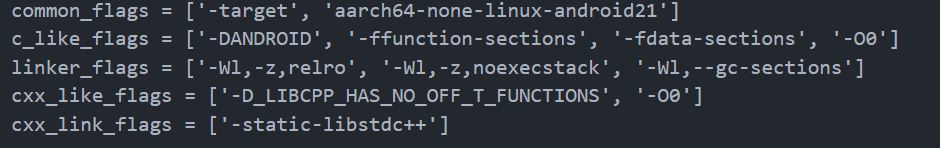
先关优化,然后去修改 subprojects\frida-core\tools 下的 post-process.py
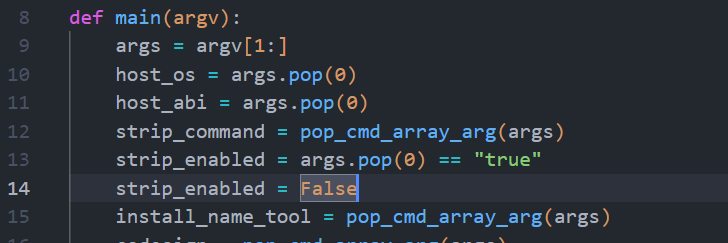
关闭 strip
然后就可以 bindiff 了
在还原大部分符号后,可以发现这个从 bytes 创建脚本,那么大胆猜测是加载明文脚本
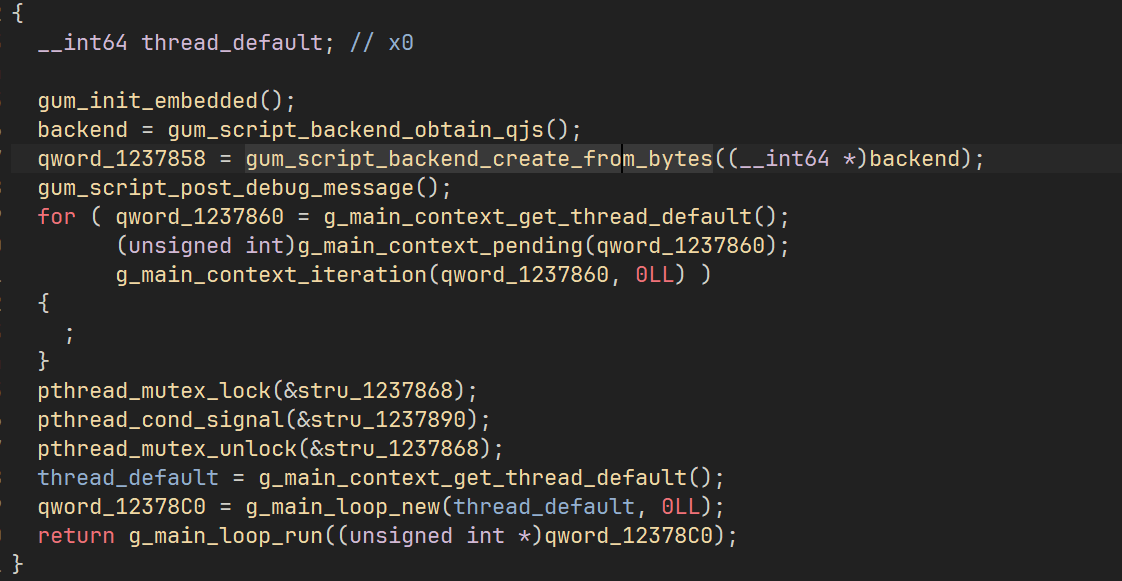
所以可以写一个脚本 dump 所有内存段,然后搜索 Java.use 定位即可
1 | Java.perform(function() { |
得到转储文件后用 010 去搜
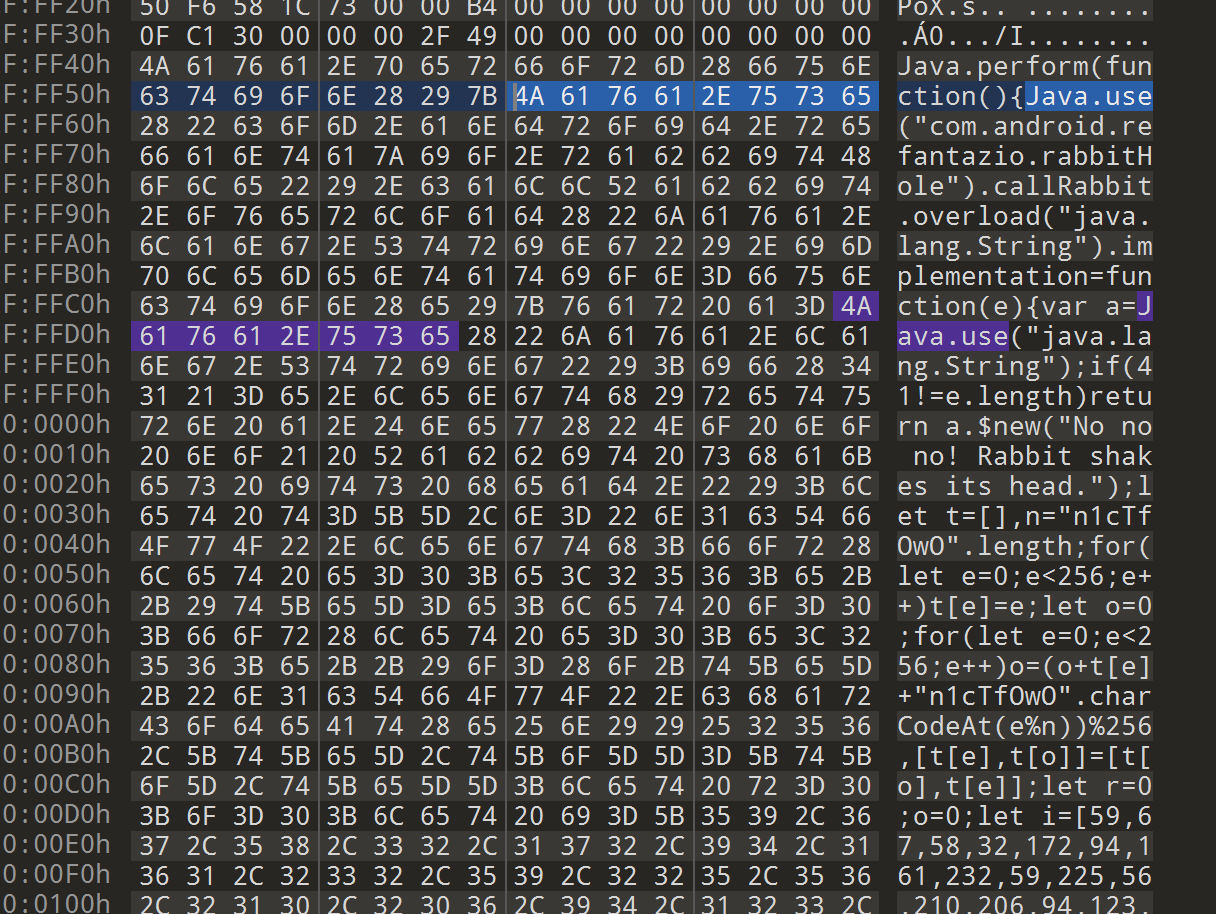
就可以秒了
1 | let t = [], |
BrokenApp
一个简单鸿蒙题目,比赛的时候没想到 add xxx 是吧 栈顶取出然后在前面加上 xxx,导致 0 加到了字符串末尾,所以就一直解不出来。。。。。。
拿到题目后第一步先反 modules.abc,这里我用的是 abc-decompiler

arkjs 层的代码是假的,关键去看 abc.def
abc.def 是被魔改了的,我们去 libark_runtime.so 分析一下
关键逻辑在这里,先把魔改的头部改回 PANDA,原本是 N1CTF

然后把输入的 flag 填入 abc.def 以 0x1B5A80 开头的 40 个字节,

然后继续加载,abc.def 没法反成 java 代码,所以我用了 abcde 反汇编,然后手动分析
1 |
|
1 | const babel = require('@babel/core'); |
