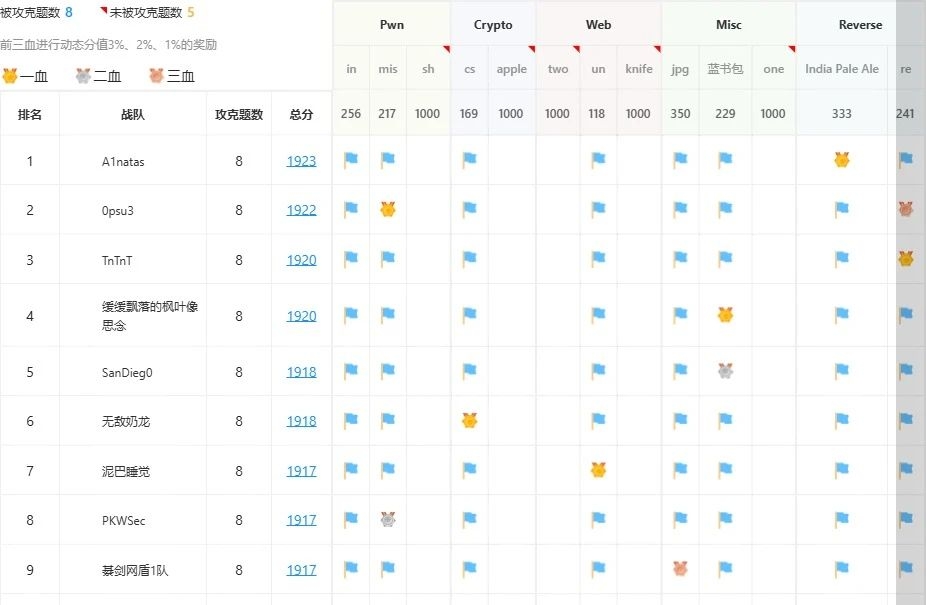
2024 古剑山网络安全大赛 Reverse 方向
台州市赛 Reverse 方向
ipa
一血嘻嘻
IOS 逆向,直接用 ida 打开分析 里面的 EasyIOS
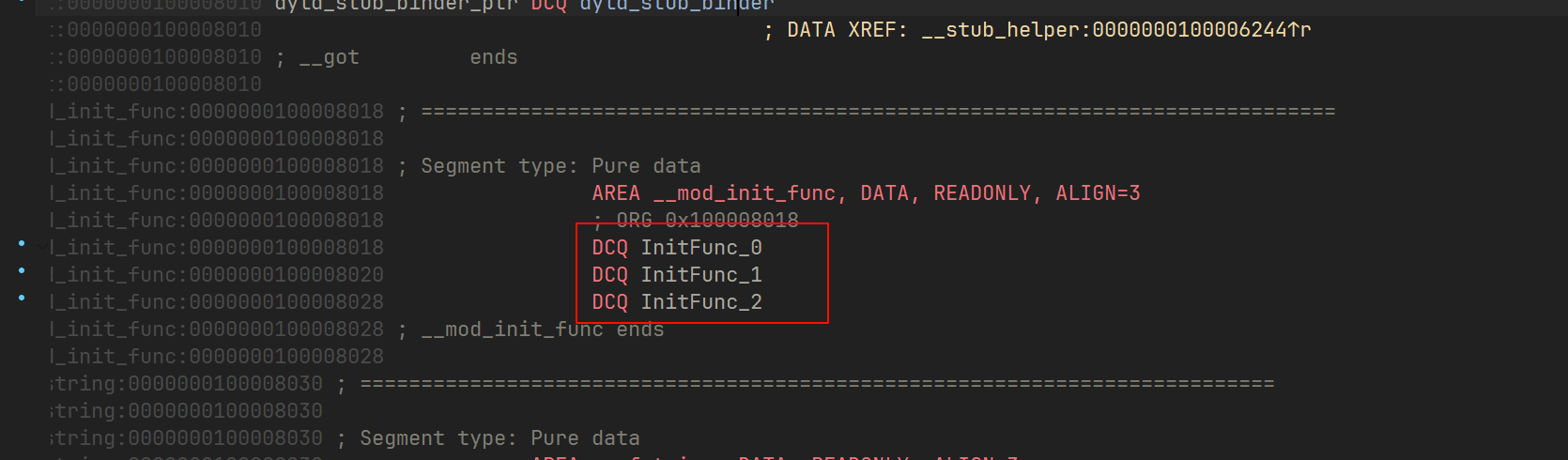
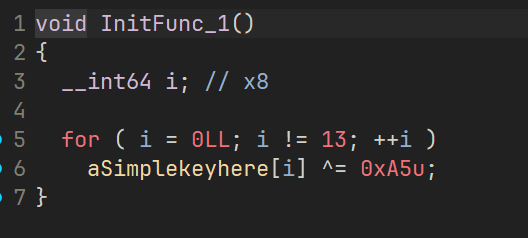
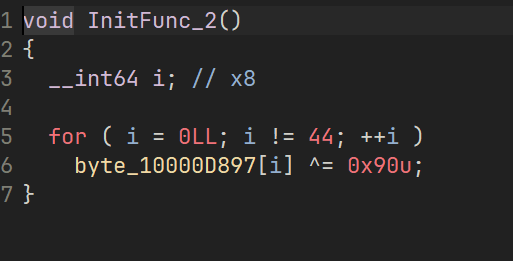
在程序段下有三个初始化程序,里面把 密文、RC4 的 key、还有 base64 的表都给修改了
1 | double InitFunc_0() |
可以得到码表 NF01ihUKST9q3lnjEBs47k2w5ad+AVHfPezg/CDyxrMLR6GvomIQJOXcpW8ZbutY
得到 base 后的密文 bExa9y+XlAbleJPlBJy5r0AFPeJQKEODCQ6D23jOpR+X
接下来写一下脚本就行了
1 |
|
这里有个问题就是这道题中的 RC4 在取 key 的时候用的是有符号字节拓展(LDRSB 指令),原本如果取模模的是 256 也就是 0xFF 那倒是不会出啥问题,但是这里模的是 250,就会导致出一点问题,得 key[i % klen] 取出来后强转成 int64 再加回去
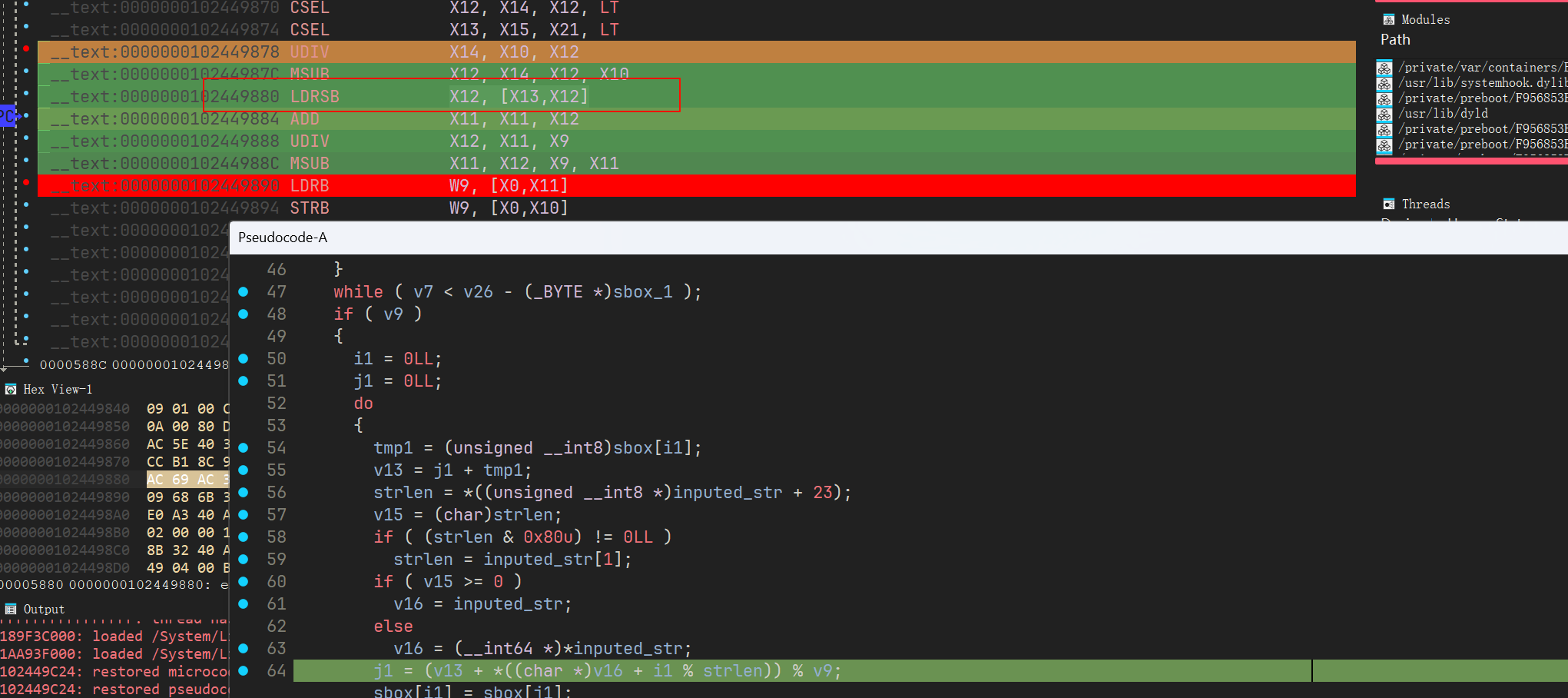
ez_re
发现有个壳,用 x32dbg 调试,下断点在 VirtualProtect 运行几次然后单步走两下断在程序段
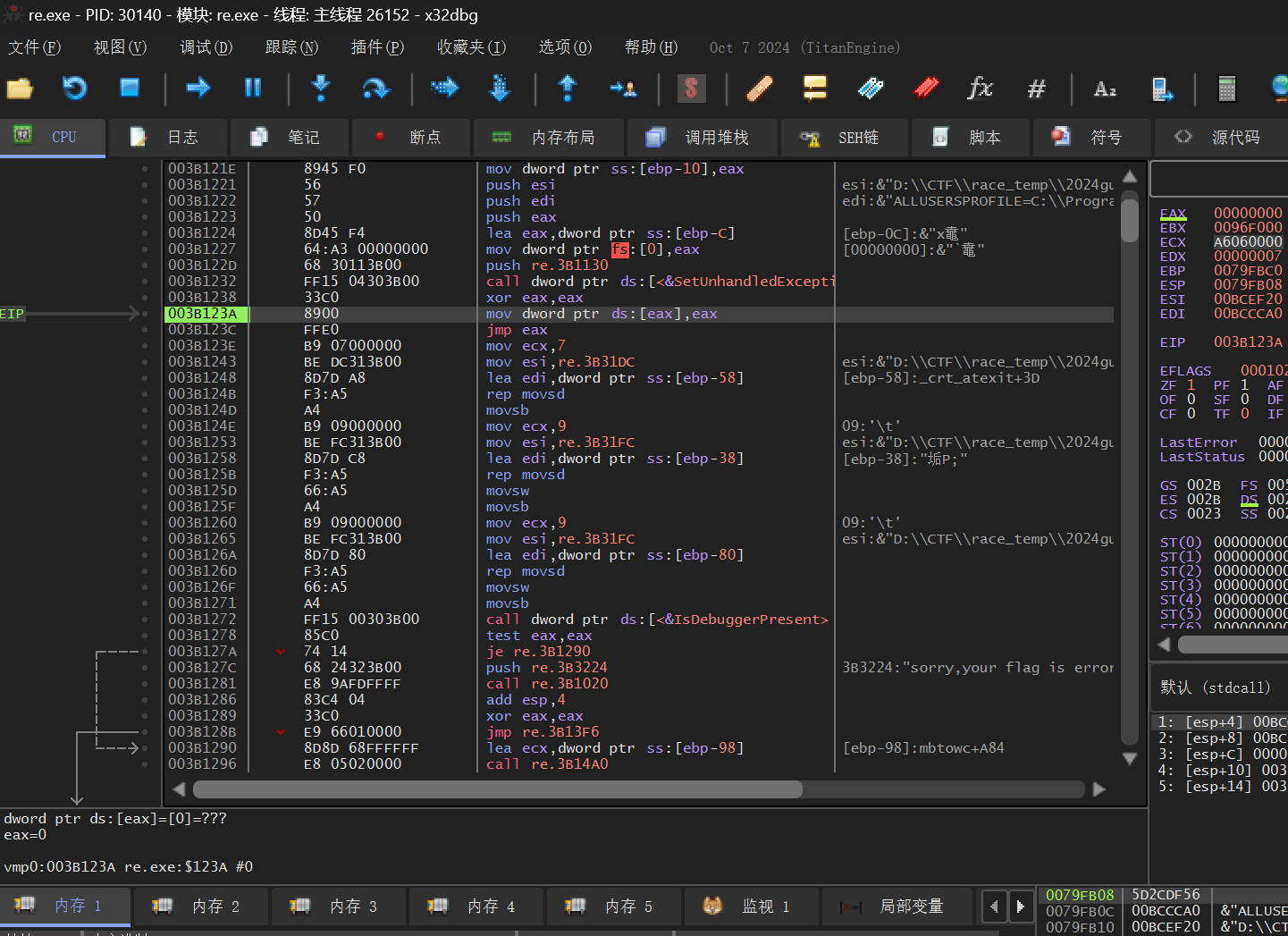
然后用 Scylla dump fix,拉进 ida 分析
手动重命名一下函数后发现,就是一个替换
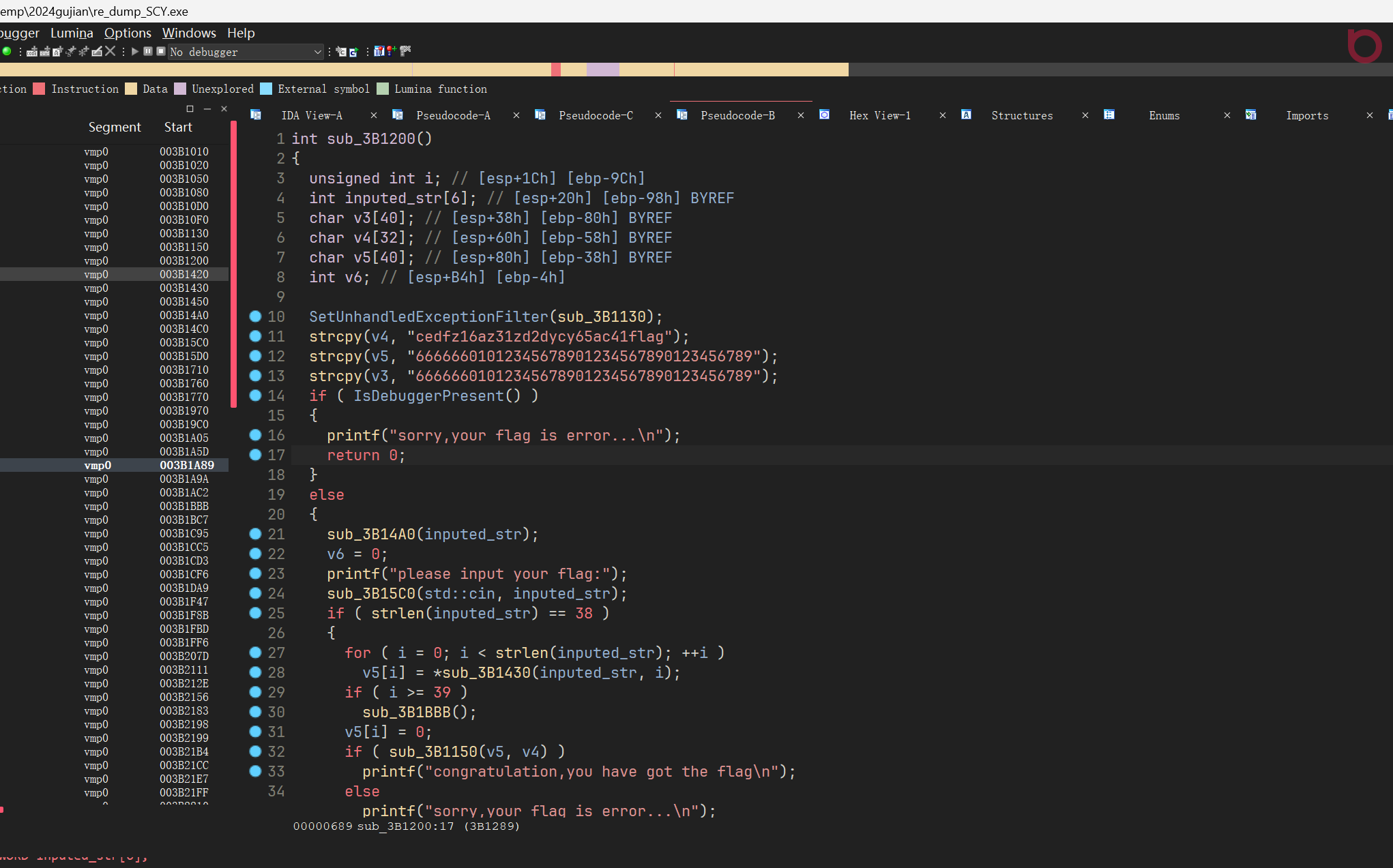
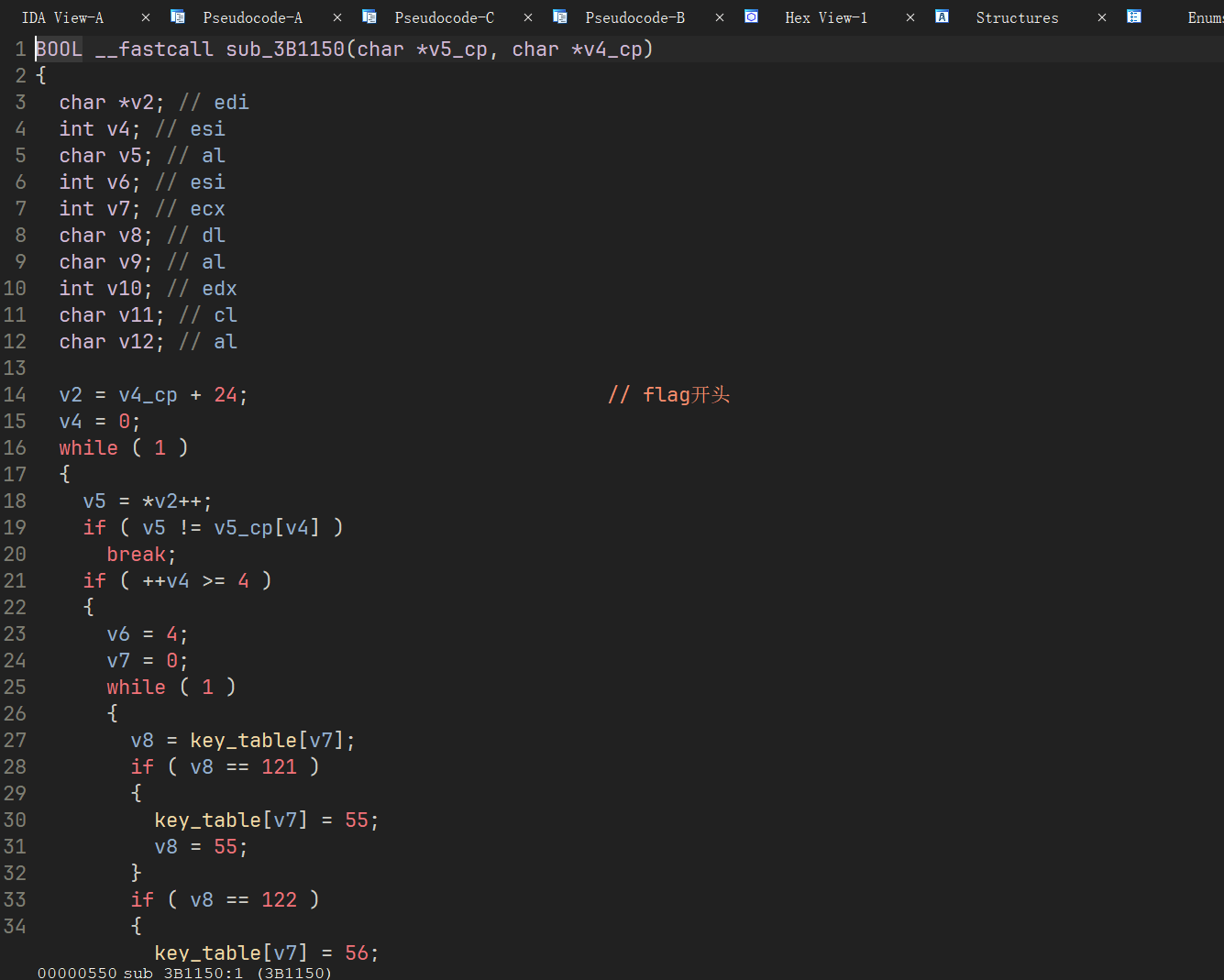
直接把伪C拉下来,改一下判断,加上打印就可以得到 Flag
1 |
|
评论
评论插件加载失败
正在加载评论插件
