Hook Fish
hook 以下 fish_fade 方法,防止删掉 dex
1 | Java.perform(() => { |
然后写解密脚本

1 | public static String decrypt(String str) { |
Fuko’s starfish
直接 Process-dump https://github.com/glmcdona/Process-Dump
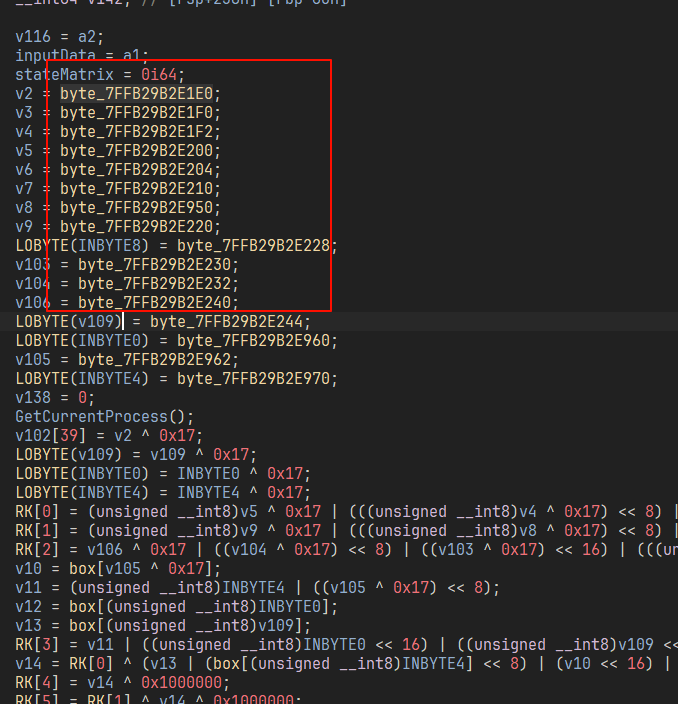
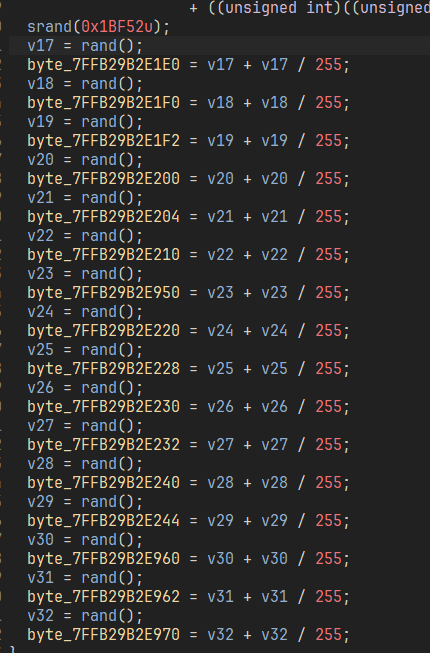
标准 aes 找到 key 异或一下 0x17 就行了
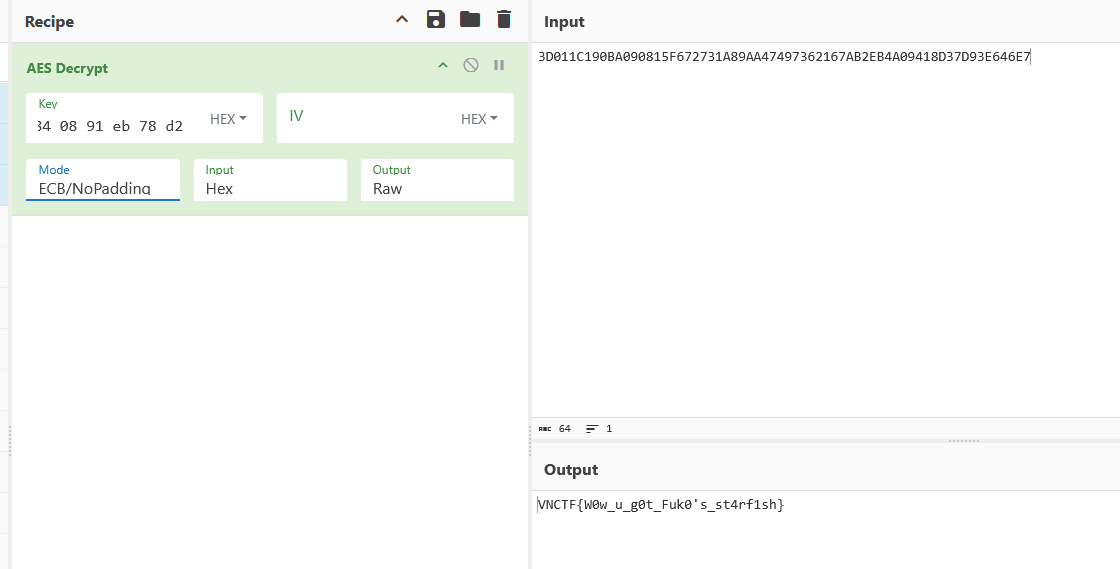
拿出来跑一下 cyberchef 解密就行了
kotlindroid
修改 JNI 的 smali,打印 add
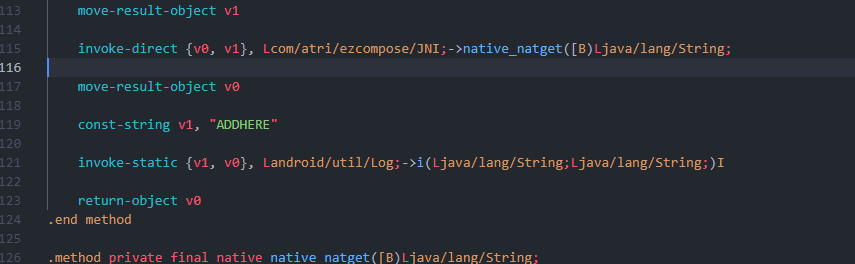
原样解密就行
1 | public static byte[] decrypt(byte[] encryptedData, byte[] key) throws Exception { |
VNCTF{Y0U_@re_th3_Ma5t3r_0f_C0mp0s3}
抽奖转盘
native 里面一个魔改 RC4(多异或了 0x40) 和 标准base64,每个字符还加了 3,ark 层每个字符异或七减一,RC4密钥 Take_it_easy,密文以 bytebuffer 的形式存在,找不到字符串
1 |
|
VNCTF{JUst_$ne_Iast_dance_2025!}
AndroidLux
busybox + proot + libexecute劫持libc函数 + 两处花指令
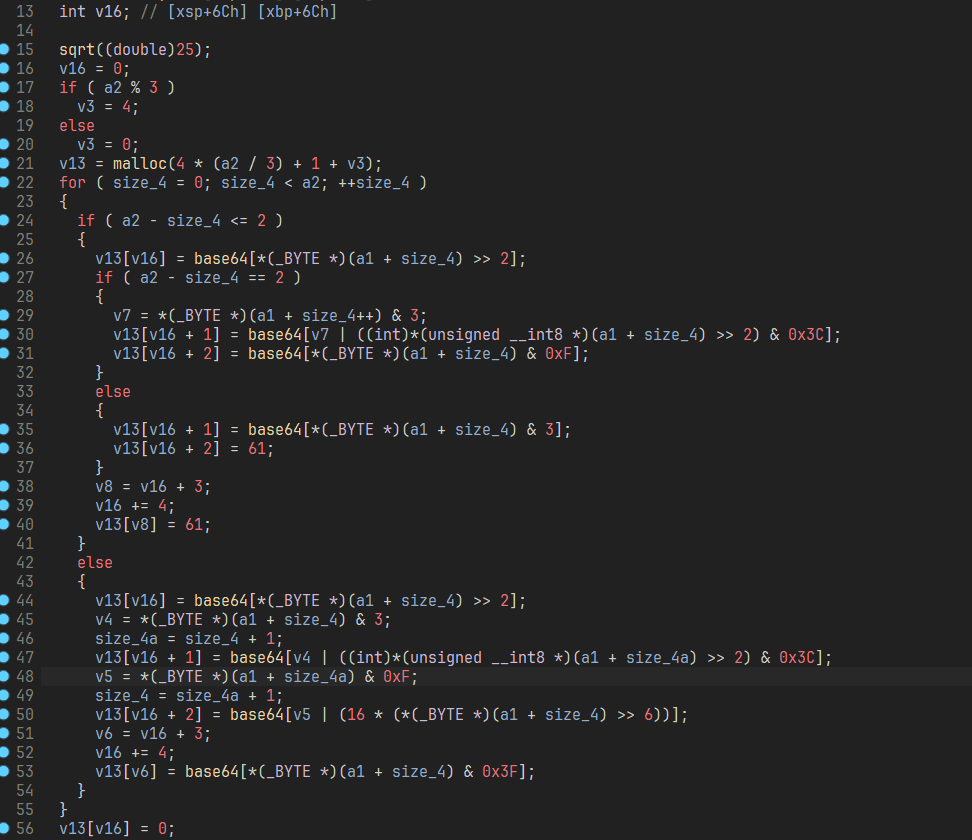
base64魔改了表分组模式,第一组六个正常取,剩下的和原版比起来等同于循环左移2bit
socket 的 recv 被魔改了 每个字节异或 1,strncmp 多了个 rot13
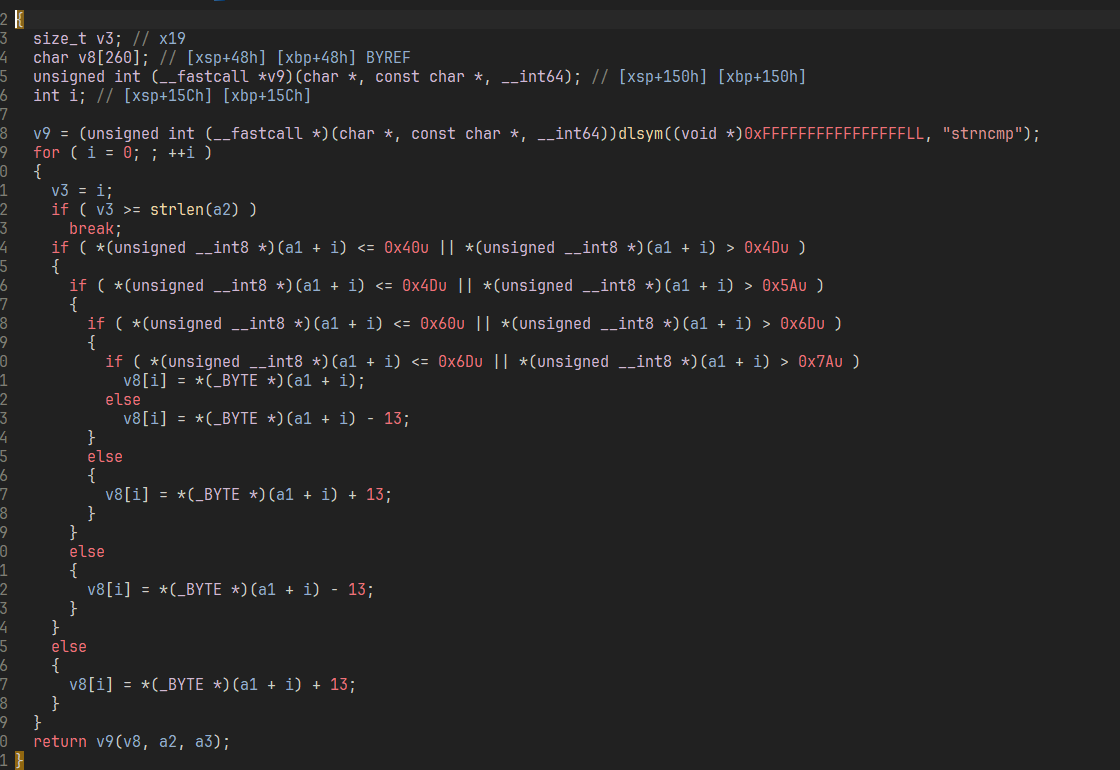
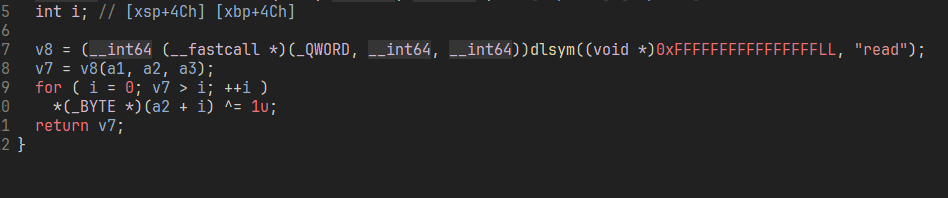
1 |
|
VNCTF{Ur_go0d_@ndr0id&l1nux_Reve7ser}
VN_Lang
直接 strings 就行了
签个到吧
写两次 shellcode 第一次构造 read 延长输入,第二次直接 getshell
1 | from pwn import * |
评论
评论插件加载失败
正在加载评论插件
